Jammin’ with James Recapped: Zero Trust with Microsoft Services, Device Trust and Security

Implementing Zero Trust for Device Security
This continues our series about implementing Zero Trust with Microsoft Services. If you missed our previous post about identity and access management, check it out now. In this guide, we will share tips to help you ensure the safety of your company’s devices.
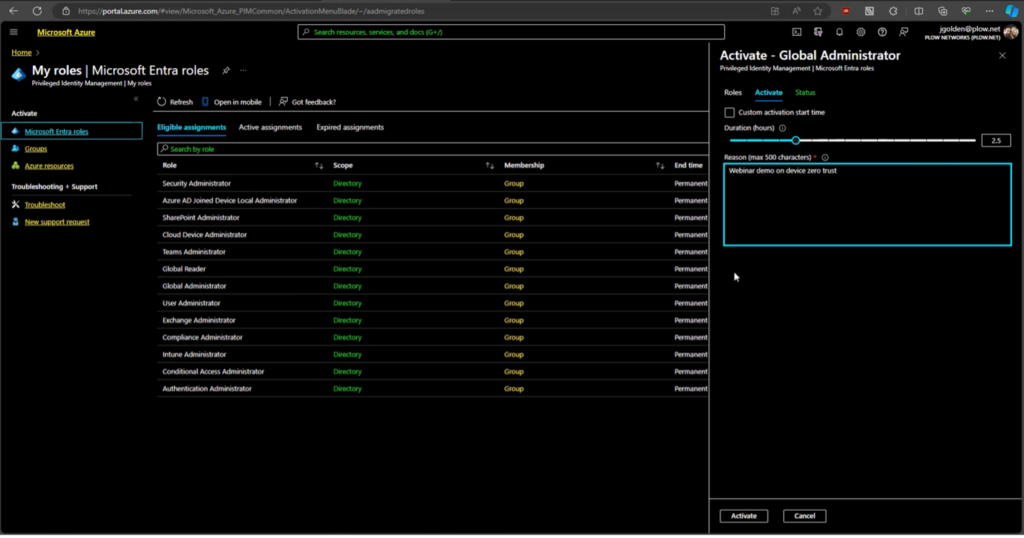
1. One way to mitigate risk is by implementing Microsoft’s Global Administrator tool. This tool forces employees to request authority to be promoted as a Global Administrator so that they may only access specific information within a certain time frame. Additionally, they must justify why they are requesting Global Administrator status. To access this tool, go to portal.azure.com and navigate to the Microsoft Entra roles page. From here, fill out the detailed information and click to activate your Global Administrator request.
2. Intune is another useful Microsoft tool that allows you to manage device configuration and ensure they adhere to policies. Go to intune.microsoft.com and click on the devices tab. Click “Manage Devices” and ” Configuration ” from here. This page will tell you which applications are deployed and allow you to create new profiles.
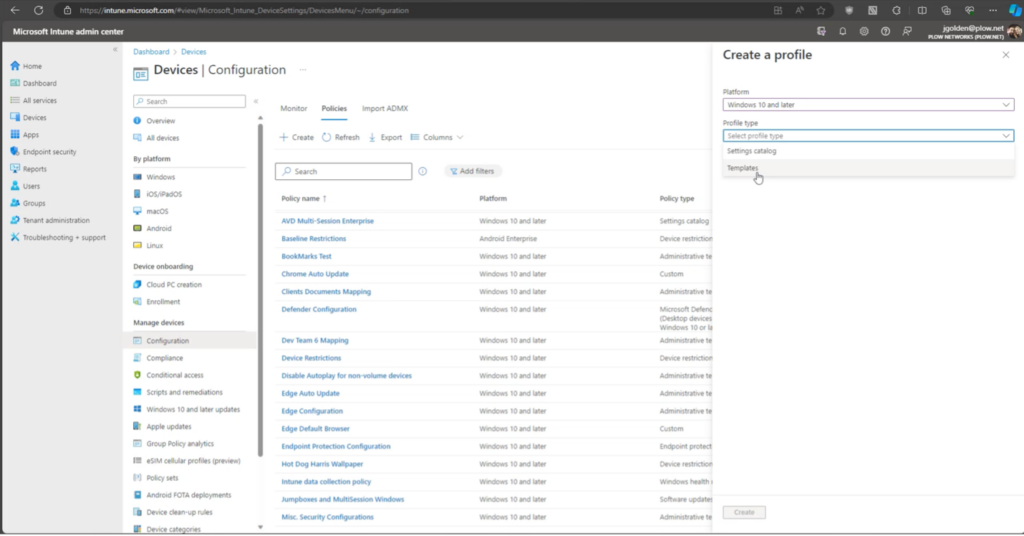
The compliance tab is also helpful and allows you to ensure that each device in your environment meets the bare minimum security requirements. For example, in our Plow network, all devices must meet the minimum OS patch version, or they cannot access information.
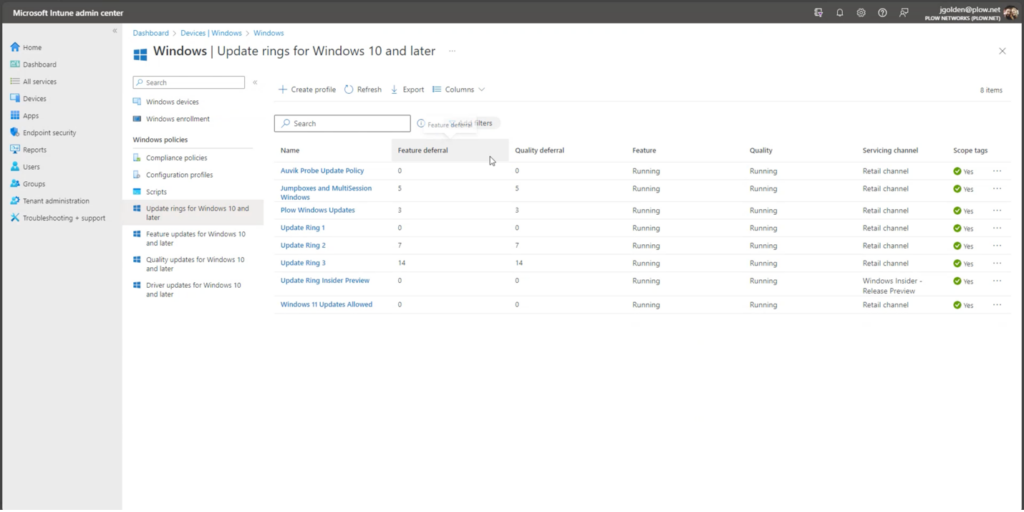
3. On the same devices page of Intune, you can update the rings for your company depending on the platform you use. Rings determine the order in which different employees in your company receive updates to their devices. We recommend that your IT people receive updates first so they can approve that the updates should be rolled out to the rest of the company.
4. When enrolling new devices to your network, navigate to the enrollment section of the devices page.
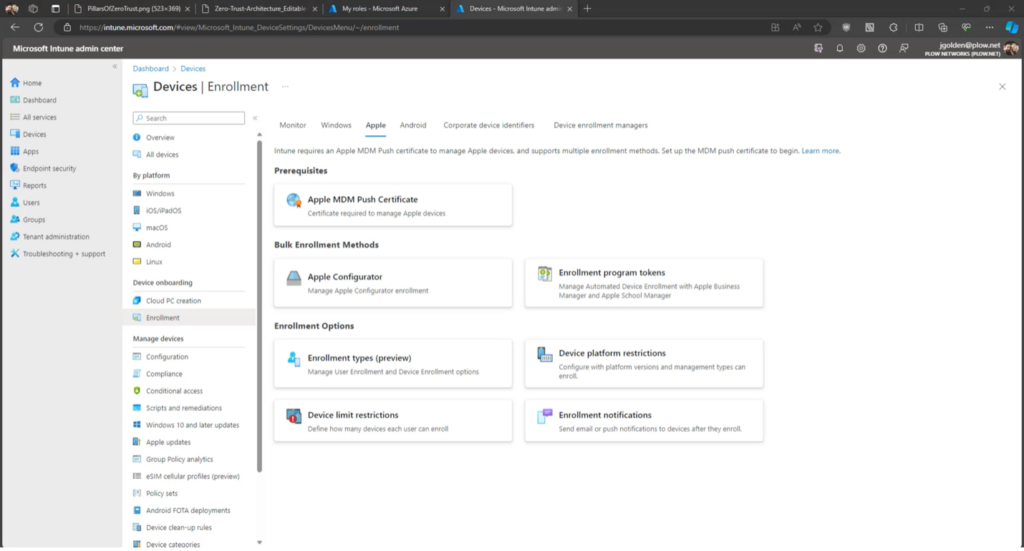
Enrollment will vary based on your company’s platform, but it is important to know if your company operates under a BYOD policy. Certain enrollment types are riskier on personal devices because they could cause personal data loss. This video explains what steps you can take to avoid an incident like this:
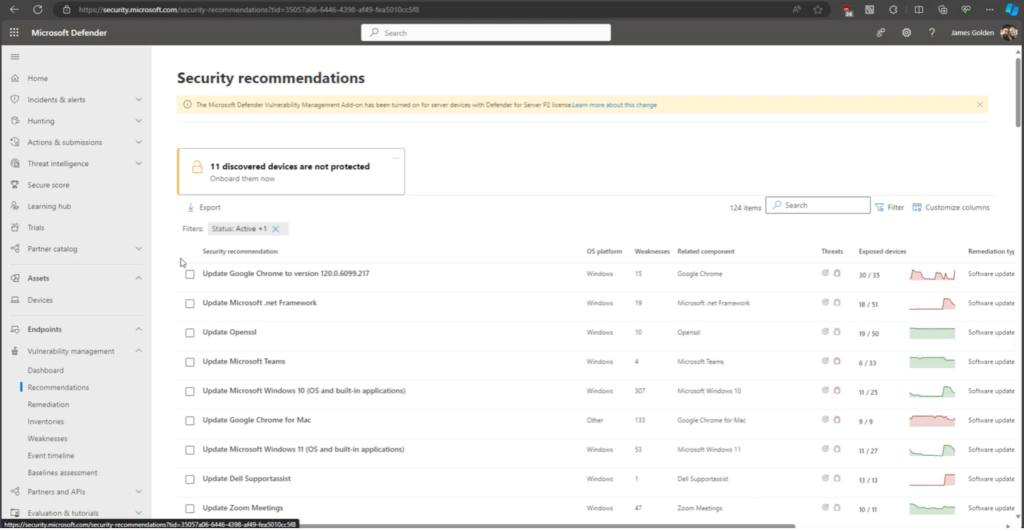
5. To check Microsoft’s recommendations for your cyber security, check out security.microsoft.com. The recommendations tab under vulnerability management provides an index for your machines and suggests what you should update within your environment. Though the page does not provide information about machine risk scores, some sections will show a percentage of potential impacts a breach would have on your environment.
By following this guide, you can implement a stronger cyber security system for your company. Register here for our next’ Jammin’ with James webinar on February 20th to learn more about Zero Trust with Microsoft Services and how your organization can optimize your Microsoft licensing.
Explore more on:





