7 Information Security Steps to Secure Hybrid Cloud Environments

Introduction
A hybrid cloud is an IT infrastructure design that integrates a company’s internal IT resources with a third-party cloud provider’s infrastructure and services. With a hybrid cloud, businesses can store data and run applications across multiple environments. Hybrid cloud environments help provision, scale, and centrally manage compute resources.
Hybrid cloud setups provide agility and scalability but can also expose organizations to potential vulnerabilities. The complexity of managing a diverse set of environments can increase the risk of data breaches, compliance failures, and operational inefficiencies.
A structured security approach is crucial for hybrid cloud environments. The diverse nature of on-premises and public cloud infrastructure requires consistent security controls across all platforms to ensure data protection, confidentiality, and availability while managing potential vulnerabilities arising from different security architectures and access points.
Understanding the Security Risks in Hybrid Cloud Environments
While hybrid cloud has many benefits, interconnecting two or more disparate cloud infrastructures will undoubtedly increase:
Increased Attack Surface: The complexity of hybrid clouds creates more potential entry points for attackers (more endpoints = more vulnerabilities), making it essential to have a comprehensive security strategy to effectively identify and mitigate threats.
Data Privacy & Compliance Risks: Many industries are governed by regulations that dictate how data must be protected and managed (e.g., GDPR, HIPAA, PCI DSS).
Visibility & Control Challenges: Organizations must maintain visibility and control over their data in a hybrid-cloud setup. Data protection helps establish governance policies and controls that dictate how data is accessed, utilized, and shared across different environments.
Integration & Configuration Risks: Maintaining precise and current records of all configurations and modifications is a cornerstone of effective security policies in the hybrid cloud computing environment. Misconfigured cloud resources, such as storage buckets left open to the public, can lead to accidental data exposure. Because this is tricky, even experienced developers can make these mistakes when juggling multiple environments.
7 Key Security Steps to Protect Hybrid Cloud Environments
Step 1: Implement Strong Identity & Access Management (IAM)
Deploy a unified IAM solution to manage user access across on-premises and cloud environments. Implement multi-factor authentication (MFA) and utilize single sign-on (SSO) for better security and efficiency.
In addition to these solutions, enforcing a Zero Trust Model for users and applications is key to securing hybrid cloud environments. This approach emphasizes the importance of ‘least privilege’ access, ensuring that users and devices are granted only necessary permissions.
Step 2: Secure Data with Encryption & Access Controls
Encrypt data at rest and in transit using robust encryption protocols. Encryption ensures that data transfer and interactions within a hybrid cloud environment are secure, so even if unauthorized users intercept your data, they won’t be able to read it.
Role-Based Access Control (RBAC) is also a key security measure that limits access to cloud resources based on the user’s role within the organization. It’s an effective method for preventing unauthorized access and accidental changes within a hybrid cloud environment.
Lastly, Data Loss Prevention (DLP) solutions help prevent unauthorized data sharing. Organizations invest significant resources in collecting and storing data. DLP solutions protect these efforts rather than letting them go to waste when data is lost or leaked.
Step 3: Continuous Monitoring & Threat Detection
Deploying Security Information and Event Management (SIEM) systems allows for real-time monitoring across your cloud environment without relying on on-premises solutions not designed for the cloud. SIEM eliminates blind spots by correlating on-premises data with cloud data to analyze end-to-end activities and detect actionable threat patterns.
Extended Detection and Response (XDR) builds on the success of EDR by automatically correlating security and event data from endpoints and other critical parts of an organization’s IT infrastructure. XDR detects and mitigates threats across cloud and on-premises environments.
Lastly, implementing automated threat intelligence solutions will proactively identify and respond to security threats across both on-premises and cloud infrastructure, ensuring continuous protection.
Step 4: Secure Cloud Workloads & Applications
Container security is the practice of securing containerized applications and infrastructure against security risks. The goal of container security is to detect, assess, and remediate misconfigurations, software vulnerabilities, and other issues that threat actors could exploit to take control of containers themselves or the systems on which they run.
Container security is similar to application security in general. It includes some of the same practices, such as scanning for vulnerabilities. Regularly scanning applications and APIs helps identify and address weaknesses before they can be exploited.
Adopting Web Application Firewalls (WAFs) and API security measures is also crucial in hybrid cloud environments to protect applications and APIs from various attacks, including those targeting vulnerabilities and malicious traffic.
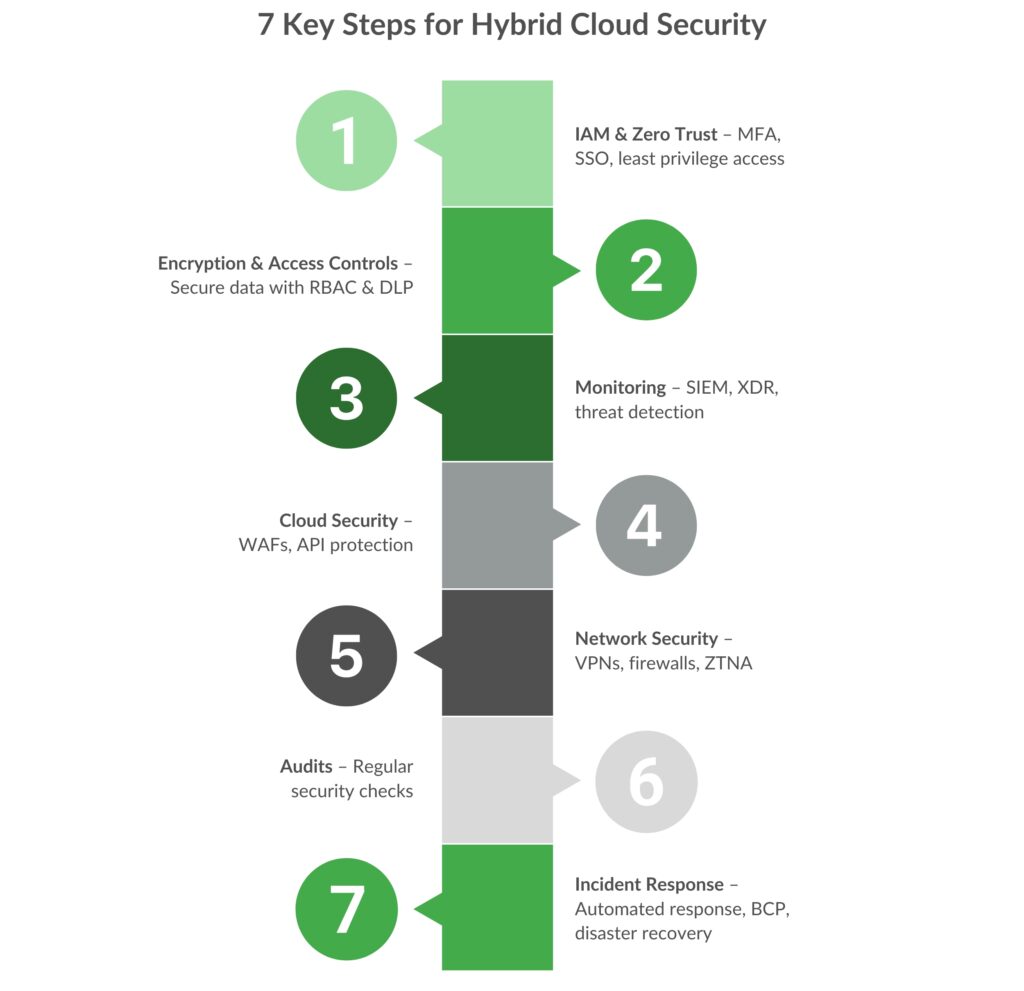
Step 5: Use Network Security Best Practices
If an adversary has already gained initial access to your infrastructure, its ability to spread its reach to more resources largely depends on network visibility. To reduce the impact area, networks can be segmented using Virtual Private Clouds (VPCs) and micro-segmentation, which expose only the resources that need public access while leaving other resources, such as databases, in private networks.
Secure connectivity can be achieved through VPNs, SD-WAN, and Zero Trust Network Access (ZTNA). Each solution offers a unique approach to securing network access and data.
Deploying firewalls and intrusion prevention systems (IPS) is also crucial to protect traffic. Firewalls act as the primary barrier against malicious traffic, and IPS provide an additional layer of defense by actively blocking threats that bypass the firewall.
Step 6: Regular Security Audits & Compliance Checks
When working across different systems, it’s easy to lose track of who has access to what or whether specific security configurations are still up to date. Audits help find gaps, misconfigurations, and potential vulnerabilities before attackers exploit them. Regular audits, such as penetration testing and vulnerability assessments, give an up-to-date picture of an organization’s security status. They also help spot minor issues before they become more significant problems.
Achieving cloud compliance with industry standards, such as NIST, GDPR, and HIPAA, requires strong security measures, regular audits, and continuous monitoring to defend against potential breaches and ensure ongoing regulatory alignment. Maintaining audit logs and security reports allows for visibility and compliance.
Step 7: Establish a Robust Incident Response & Recovery Plan
Cloud incident response is a strategic approach to detecting and recovering from cyberattacks on cloud-based systems. It comprises a coordinated series of procedures to help you detect threats, eradicate malicious actors, and recover from an incident in an organized, efficient, and timely manner.
Automated response mechanisms use software and algorithms to monitor, detect, and respond to security incidents without human intervention. It automates repetitive tasks, allowing rapid response to threats and, therefore, containing security breaches.
A business continuity plan (BCP) supported by disaster recovery (DR) could be the difference between successfully navigating a disaster and folding because of one. Regularly testing these plans helps minimize the financial implications of data loss or critical failure.
Conclusion
As we’ve learned, hybrid cloud security is an all-encompassing term that includes the technology and best practices used to protect critical and confidential data, applications, and IT resources.
The seven steps outlined in this post will help strengthen your hybrid cloud environment’s data security, compliance, and operational resilience. A partitioned yet connected security strategy will allow your business to decide which processes are guarded in the private cloud and which workloads are on the public cloud.
Plow Networks’ managed services protect your hybrid cloud environment before, during, and after migration. They can help your organization reduce the risk of exposing sensitive data to cyberattacks and severe damage from data breaches.
Explore more on:





